
I would like to welcome you to my cybersecurity blog. Dive into a world where every byte counts and every click matters. As a dedicated learner in the vast field of cybersecurity, I share my discoveries, insights, and the occasional epic fail; hey, learning curves! Whether you’re a fellow newbie or a seasoned pro looking for fresh perspectives, join me on this adventure. Let’s level up our knowledge together! Start reading my latest articles now!
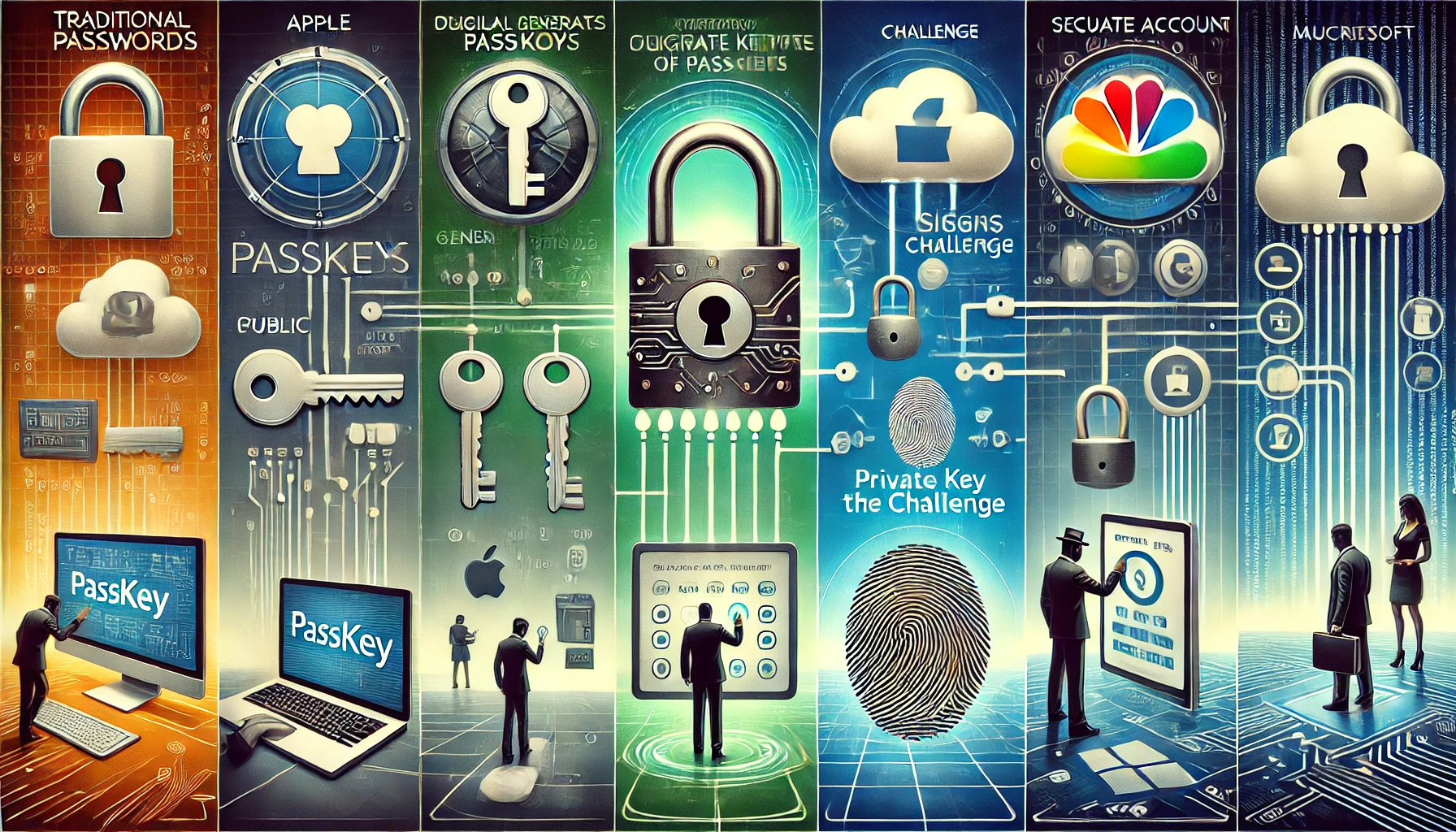
A deep dive into passkeys
Discover the future of digital security with passkeys, a revolutionary shift from traditional passwords, offering unparalleled protection against cyber threats. Dive into the comprehensive guide that explores how passkeys are transforming online authentication in 2024 and beyond.
Read More

BIOS vs. UEFI
BIOS has been the standard for decades, but UEFI offers superior security features like secure boot, faster boot times, and better compatibility with modern hardware. As cyber threats grow more sophisticated, upgrading to UEFI is becoming essential for protecting your system. In 2024, making the switch to UEFI could be a critical step in safeguarding your digital assets.
Read More

ICMP protocol decoded
The Internet Control Message Protocol (ICMP) is a crucial communication protocol that serves as the backbone for diagnostic and error-reporting activities across the internet. In this comprehensive article, I will dive deep into the ICMP protocol's technical specifics and explore its practical use cases.
Read More

Cyberinsurers market 101
In 2024, the cyber insurance market is still rapidly growing as businesses face increasing cybersecurity threats, from data breaches to ransomware. With coverage options like business interruption and regulatory fines, companies are seeking protection against financial losses. Explore key trends, pricing, and the evolving landscape of cyber insurance in my latest blog post.
Read More
IPv6 adoption in 2024
In 2024, the global internet landscape continues its gradual shift from IPv4 to IPv6, a transition driven by the exhaustion of IPv4 addresses and the exponential growth of internet-connected devices.
Read More
Previous
Next





