Telnet vs. SSH cheat sheet
4 July 2024

In the field of remote network management, it’s crucial to understand the complexities of various network protocols involved. Today, we’ll explore two fundamental protocols: Telnet and Secure Shell (SSH).
Overview of each protocol
Telnet protocol
Definition: Telnet (TELecommunication NETwork) is a protocol used to provide bidirectional interactive text-oriented communication via a virtual terminal connection.
Purpose: Telnet allows users to remotely control a computer over a network, making it a handy tool for network administrators.
Key features:
- Plaintext transmission: data is sent in plain text, making it easy to implement but insecure.
- Minimal overhead: simplistic design with minimal protocol overhead.
- Simple command structure: easy to use with straightforward commands.
Typical use cases:
- Remote management of devices: accessing network devices like routers and switches.
- Legacy systems access: managing older systems that do not support secure protocols.
- Network device configuration: quick changes and troubleshooting in secure environments.
Secure shell (SSH) protocol
Definition: SSH (secure shell) is a protocol that provides secure command-line interface access over an unsecured network.
Purpose: SSH is designed to enable secure remote login and other secure network services over an insecure network, making it essential for modern network management.
Key features:
- Encrypted communication: ensures data is transmitted securely using encryption.
- Secure authentication: supports strong authentication methods.
- Robust command execution: allows secure command execution and file transfers.
Typical use cases:
- Secure remote administration: managing servers and network devices securely.
- Secure file transfers: using SCP (secure copy protocol) or SFTP (secure file transfer protocol).
- Encrypted communications: setting up secure tunnels for data transmission.
Comparison analysis
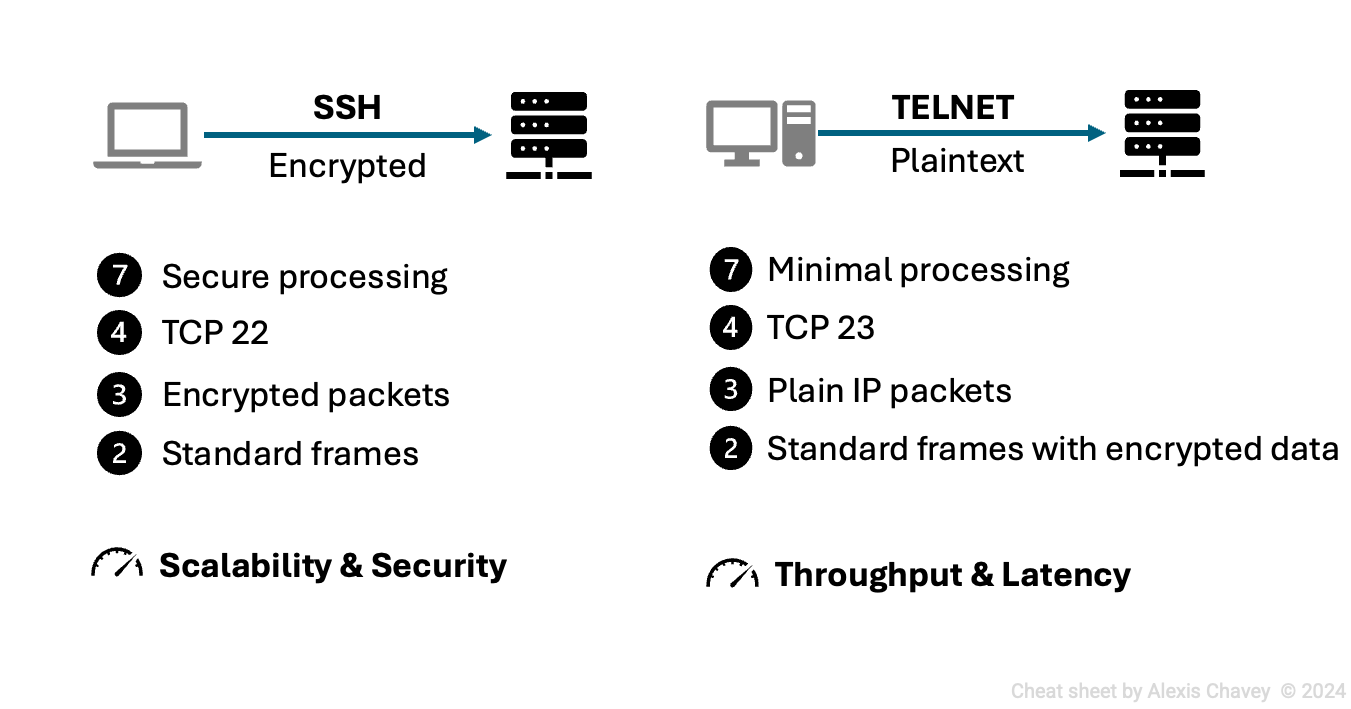
Application layer
Telnet
- Functionality: provides a basic, plaintext interface for remote control.
- Involved protocols: uses the Telnet protocol itself.
- Data format and processing: transmits data in plain text, making it vulnerable to interception.
SSH
- Functionality: provides secure, encrypted communication for remote control and file transfers.
- Involved protocols: utilizes SSH along with SCP and SFTP for secure file transfers.
- Data format and processing: encrypts data before transmission, supporting various encryption algorithms like AES, 3DES….
Transport layer
Telnet
- Connection mechanisms: connection-oriented, using TCP.
- Error checking and flow control: relies on TCP for error checking and flow control.
- Involved protocols: operates over TCP, typically on port 23.
SSH
- Connection mechanisms: connection-oriented, using TCP.
- Error checking and flow control: utilizes TCP for reliable data transmission.
- Involved protocols: operates over TCP, typically on port 22.
Internet layer
Telnet
- Routing and addressing mechanisms: standard IP routing and addressing.
- Involved protocols: uses IP for packet delivery.
- Packet structure: plaintext data encapsulated in IP packets.
SSH
- Routing and addressing mechanisms: standard IP routing and addressing.
- Involved protocols: uses IP for packet delivery.
- Packet structure: encrypted data encapsulated in IP packets.
Network access layer
Telnet
- Data link and physical layer functions: relies on standard Ethernet or other data link protocols.
- Involved protocols: standard data link protocols like Ethernet and ARP.
- Frame structure: standard Ethernet frames containing IP packets.
SSH
- Data link and physical layer functions: similar reliance on standard Ethernet or other data link protocols.
- Involved protocols: standard data link protocols like Ethernet and ARP.
- Frame structure: standard Ethernet frames containing encrypted IP packets.
Performance metrics
Throughput:
- Telnet: higher throughput due to lack of encryption overhead. It allows for faster data transmission but compromises security.
- SSH: slightly lower throughput because of encryption/decryption processes. Security measures add some overhead, affecting speed.
Latency:
- Telnet: lower latency due to minimal processing. Quick response times can be beneficial in controlled environments.
- SSH: slightly higher latency due to encryption overhead. The encryption and decryption processes add some delay.
Reliability:
- Telnet: relies on TCP for reliable delivery. Ensures data packets are delivered accurately but without security.
- SSH: also relies on TCP, providing reliable delivery with the added layer of security.
Scalability:
- Telnet: scalable in terms of simplicity and minimal overhead, but the lack of security limits its use in large deployments.
- SSH: highly scalable with built-in security features, making it suitable for large-scale, secure deployments.
Security:
- Telnet: lacks security features, making it susceptible to eavesdropping and interception.
- SSH: provides robust security through encryption and secure authentication, protecting data from unauthorized access.
Security features
Authentication mechanisms:
- Telnet: uses basic username/password authentication transmitted in plaintext, which can be easily intercepted.
- SSH: supports public key authentication, encrypted passwords, and multifactor authentication, offering a high level of security.
Encryption methods:
- Telnet: none. All data is sent in plain text.
- SSH: uses strong encryption algorithms such as AES (advanced encryption standard), 3DES (triple data encryption standard), and Blowfish to secure data.
Vulnerabilities and mitigation strategies:
- Telnet: highly vulnerable to eavesdropping, man-in-the-middle (MitM) attacks, and unauthorized access. Mitigation includes using SSH for secure communications.
- SSH: more secure but can be vulnerable to outdated algorithms or poor key management. Mitigation strategies include using strong, updated encryption methods and proper key management practices.
Implementation and configuration
Ease of setup:
- Telnet: simple to set up due to minimal configuration requirements. Suitable for quick or/and temporary access needs.
- SSH: slightly more complex due to the need for key management and configuration of security settings. Ensuring optimal security requires proper setup.
Compatibility:
- Telnet: highly compatible with legacy systems. Often used where legacy hardware and software are still in use.
- SSH: widely compatible across modern systems, though older systems may require updates to support SSH.
Tools and software support:
- Telnet: basic Telnet clients are available on most platforms, offering minimal features.
- SSH: Widely supported by robust clients such as OpenSSH, PuTTY, and various commercial solutions, offering extensive features and customization options.
Use cases scenarios
Best use cases for Telnet:
- Access to legacy systems: ideal for environments where encryption is not a concern, and for older systems that need to be managed.
- Quick, temporary access: suitable for quick changes and troubleshooting in secure, isolated environments.
Examples:
- Network administrators accessing old switches and routers for configuration changes.
- IT professionals managing older servers that do not support modern secure protocols.
- Quick temporary access to network devices within a controlled, secure environment.
Best use cases for SSH:
- Secure remote administration: managing servers and network devices securely over an unsecured network.
- Secure file transfers: using SCP or SFTP to transfer files securely between systems. Encrypted communications: setting up secure tunnels for data transmission.
Examples:
- System administrators managing Linux servers remotely with command-line access.
- Developers securely transferring files between development and production environments using SCP or SFTP.
- Network engineers setting up encrypted tunnels for secure communications between network segments.
Scenarios for either protocol:
Internal network management: where security policies allow plaintext communication (Telnet) or require encryption (SSH).
Examples:
- Managing internal devices within a highly secured network where encryption is not mandatory.
- Utilizing SSH for sensitive data transfers and Telnet for quick, low-risk operations in secure environments.
Pros and cons
Telnet:
- Strengths: Simplicity: easy to set up and use. Minimal overhead: low resource consumption. Legacy support: compatible with older systems.
- Weaknesses: Lack of security: data is transmitted in plain text. Vulnerability: susceptible to eavesdropping and interception. Limited use: not suitable for public or insecure networks.
SSH:
- Strengths: Security: provides encrypted communication and secure authentication. Versatility: supports secure file transfers and command execution. Scalability: suitable for large deployments requiring high security.
- Weaknesses: Complexity: slightly more complex to set up. Overhead: encryption and decryption processes add some overhead. Compatibility: older systems may require updates to support SSH.
Captain Obvious : use SSH!
Telnet and SSH serve similar purposes but differ vastly in terms of security. Telnet is simple and fast but lacks security features, making it suitable only for secure, isolated environments. SSH, on the other hand, provides robust security through encryption and secure authentication, making it ideal for secure remote administration and data transfer over unsecured networks.