FTP vs SFTP
3 August 2024
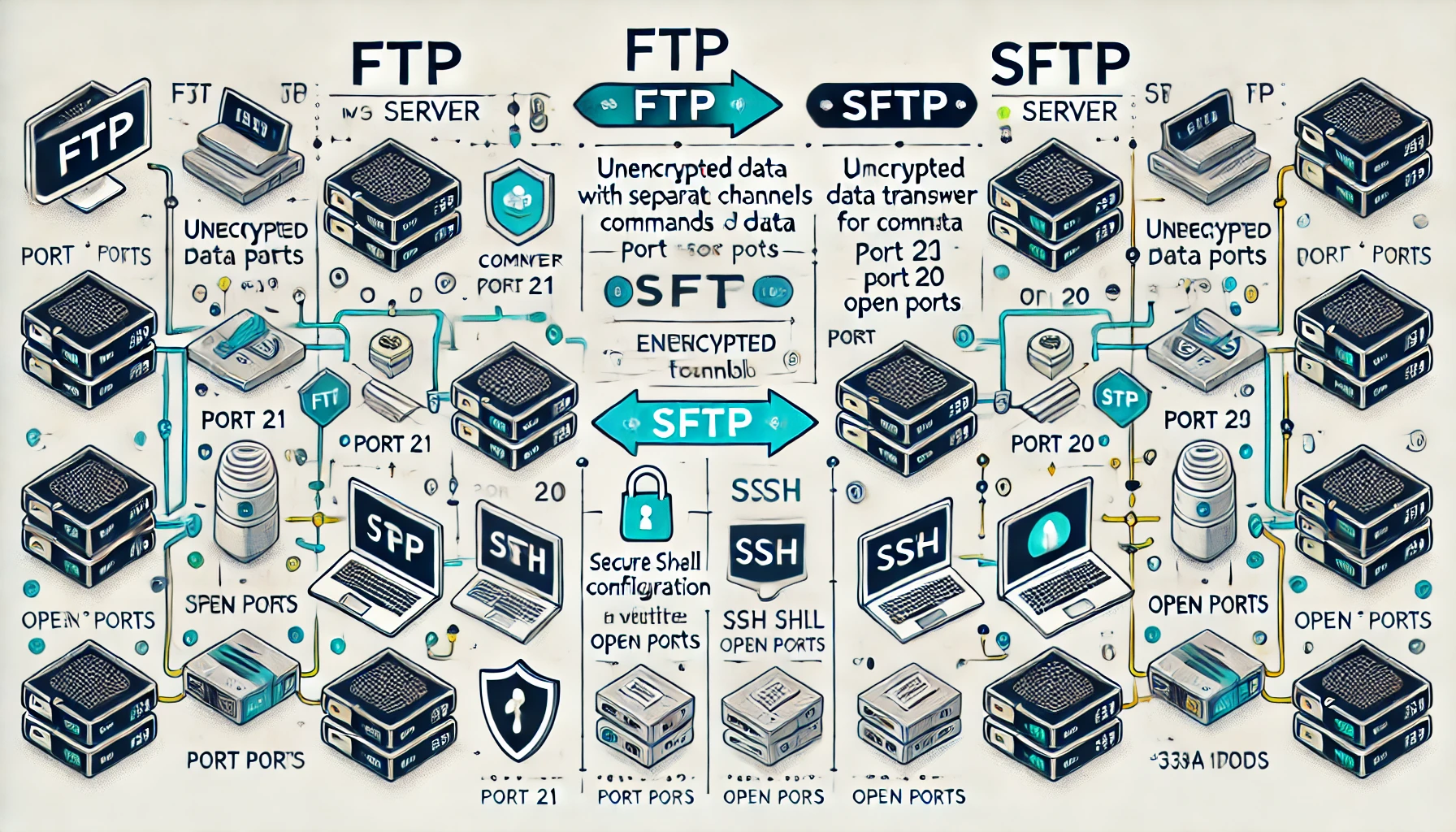
Comprehensive comparison between FTP and SFTP
To ensure secure and efficient data transfer, it’s important to understand the differences between FTP (File Transfer Protocol) and SFTP (Secure File Transfer Protocol) when transferring files. This detailed comparison explores the technical aspects, security implications, and operational modes of each protocol, enhanced by real-world examples.
Understanding FTP
File Transfer Protocol (FTP) is a standard protocol used for transferring files between a client and a server over a network. It uses two separate channels: a command channel for sending commands and a data channel for transferring data. Typically, FTP operates over ports 20 and 21.
Key features of FTP
- Unencrypted transmission: FTP transmits data in plain text, making it vulnerable to interception and eavesdropping.
- Dual channels: uses separate channels for commands (port 21) and data (port 20), complicating firewall configurations.
- Authentication: relies on basic username and password authentication, which is not secure unless combined with FTPS (FTP Secure).
- File transfer capabilities: supports resuming interrupted transfers and handles various file types and structures.
Understanding file transfer capabilities
File types
- Binary files: these include images, executables, videos, and any other non-text files. FTP handles binary files by transferring them in a way that preserves their exact original state, ensuring that no data is altered or corrupted during the transfer.
- Text files: these include plain text files, HTML, XML, and other text-based documents. FTP can transfer text files in ASCII mode, which can adjust the line endings based on the operating systems of the source and destination, ensuring compatibility.
- Compressed files: FTP can handle files that have been compressed using various algorithms, such as ZIP or TAR files, maintaining their compressed state during transfer.
File structures
- Flat files: these are simple files with no internal structure other than lines of text. FTP can transfer these files without modification.
- Hierarchical files: FTP can transfer entire directory structures, maintaining the hierarchy of folders and subfolders. This is useful for transferring complex websites, applications, or any organized set of files.
- Binary Large Objects (BLOBs): FTP can handle the transfer of large data objects, which are often used in databases or large datasets.
Resuming interrupted transfers
- Checkpointing: FTP supports the ability to resume a file transfer from the point where it was interrupted. This is achieved through the use of FTP commands like
REST(restart) andRETR(retrieve). If a transfer is interrupted, the client can send aRESTcommand to the server indicating the point at which to resume, followed by aRETRcommand to continue the transfer from that point. - File size and transfer status: by maintaining metadata about the file size and the amount of data transferred, FTP clients can efficiently resume transfers without re-transmitting data, saving bandwidth and reducing transfer times.
Use cases
-
Transferring a website: a website consists of HTML files, CSS stylesheets, JavaScript files, images, and possibly video content. FTP can transfer these files while maintaining the directory structure, ensuring that all files are correctly placed in their respective folders on the server.
-
Uploading large databases: for databases that are backed up into large BLOB files, FTP can transfer these without corruption. If the transfer is interrupted, it can be resumed, ensuring that the entire database is uploaded without starting from scratch.
-
Software distribution: distributing software updates or patches often involves transferring large binary files. FTP ensures these files are transferred accurately and can resume if the connection drops, avoiding the need to restart the transfer.
Understanding SFTP
Secure File Transfer Protocol (SFTP), developed in the late 1990s, leverages the Secure Shell (SSH) protocol to provide secure file transfer. SFTP operates over a single channel (port 22), ensuring that all data, commands, and credentials are encrypted during transfer.
Key features of SFTP
- Encrypted transmission: encrypts both commands and data, ensuring secure file transfers.
- Single channel: uses a single channel for all operations, simplifying firewall configurations and enhancing security.
- Robust authentication: supports multiple authentication methods, including password, public key, and multi-factor authentication.
- Data integrity: ensures data integrity through cryptographic methods, protecting against tampering and interception.
FTPS is not SFTP !
Both FTPS and SFTP offer secure file transfer capabilities, but they are totally different animals. FTPS is useful for organizations needing to comply with standards that require SSL/TLS or those that need to integrate with existing FTP infrastructure. SFTP, on the other hand, offers a more streamlined and robust solution, particularly suited for environments where security and simplicity are required.
FTPS aka FTP Secure
FTPS is an extension of the traditional File Transfer Protocol (FTP) that adds support for the Transport Layer Security (TLS) and the Secure Sockets Layer (SSL) cryptographic protocols.
Key Features
- Encryption: FTPS encrypts both the command and data channels using SSL/TLS, providing protection against eavesdropping and tampering.
- Authentication: supports various authentication methods, including username/password, client-side certificates, and server-side certificates.
- Port usage: FTPS uses multiple ports. The control connection is established on port 21, while data connections use a range of ports negotiated during the session. This can complicate firewall configurations.
- Connection modes: supports both explicit and implicit modes:
- Explicit FTPS (FTPES): the client explicitly requests security from the FTPS server by sending an
AUTH TLScommand before login. - Implicit FTPS: the client connects to a different port (usually port 990) and starts an SSL/TLS handshake without any prior negotiation.
- Explicit FTPS (FTPES): the client explicitly requests security from the FTPS server by sending an
Differences
Underlying protocol
- FTPS: an extension of FTP using SSL/TLS for security.
- SFTP: a subsystem of SSH providing secure file transfers.
Port usage
- FTPS: uses multiple ports (21 for commands and a range of ports for data).
- SFTP: uses a single port (port 22).
Authentication
- FTPS: supports username/password and certificate-based authentication.
- SFTP: supports password and SSH key-based authentication, with strong emphasis on public key authentication.
Firewall configuration
- FTPS: requires more complex firewall rules due to multiple ports.
- SFTP: easier firewall configuration with a single port.
Data integrity and security
- FTPS: provides good security through SSL/TLS but can be more challenging to configure securely.
- SFTP: provides robust security and is generally easier to secure correctly due to its use of SSH.
Active vs. passive modes for FTP and FTPS
Both FTP (File Transfer Protocol) and FTPS (FTP Secure) support active and passive modes for data transfer, accommodating different network configurations and firewall requirements. I try to provide you with a quick overview of how these modes work for both protocols and why they are used.

Active mode
How it works
-
Client connection: in both FTP and FTPS, the client opens a random port above 1023 and sends the
PORTcommand to the server, specifying the client’s IP address and port number. -
Server connection: the server initiates a connection from its port 20 to the client’s specified port for data transfer.
Security implications
Active mode can be problematic for clients behind a firewall or NAT (Network Address Translation) because it requires the firewall to allow incoming connections from the server to the client’s random port. This can expose the client to security risks if the firewall configuration is not handled carefully.
Use case
Active mode might be used in controlled environments where the firewall settings are known and can be configured accordingly.
Passive mode
How it works
- Client connection: in both FTP and FTPS, the client initiates both control and data connections. It sends the
PASVcommand to the server, which responds with an IP address and port number. - Server connection: the server listens on a random port above 1023 and sends this port information back to the client. The client then initiates a connection to this port for data transfer.
Security implications
Passive mode is more firewall-friendly because all connections are initiated by the client. This makes it easier for clients behind firewalls or NAT to connect without the need for special configurations.
Use case
Passive mode is generally preferred for its ease of configuration and compatibility with firewalls, making it suitable for most real-world applications.
Why active and passive modes are needed ?
Both FTP and FTPS use separate command and data channels. This fundamental structure necessitates the use of active and passive modes to manage how these connections are established, especially through firewalls.
-
Active mode: provides a method where the server connects back to the client for data transfer, useful in controlled internal networks.
-
Passive mode: simplifies connections for clients behind firewalls or NATs by allowing the client to initiate all connections. This mode is particularly beneficial for external and public network connections.
FTPS specific considerations
-
FTPS adds SSL/TLS encryption to both command and data channels, providing secure data transfers. Despite this, it retains the same active and passive mode structures as FTP.
-
Active mode FTPS: requires careful firewall configuration to allow incoming connections from the server, which can be challenging and less secure.
-
Passive mode FTPS: easier to manage in terms of firewall configuration, as it involves fewer open ports on the client side, enhancing security and simplifying setup.
Use cases
-
Active mode FTP/FTPS: used in an internal network where firewall settings can be strictly controlled, ensuring secure connections through predefined ports.
-
Passive mode FTP/FTPS: ideal for external connections over the internet, where client devices may be behind various firewalls and NATs, ensuring ease of connectivity and enhanced security.
Conclusion
When deciding between FTP and SFTP, consider the specific security and compliance needs of your organization. While FTP may suffice for non-sensitive data transfers, SFTP is essential for secure, compliant transfers of sensitive information.
Understanding the active and passive modes in FTP and FTPS is crucial for configuring secure and efficient file transfers. Active mode can be useful in controlled environments but poses challenges with firewalls. Passive mode, preferred for its firewall compatibility and security, is suitable for most scenarios, especially where clients are behind firewalls or NAT.
FTPS, while adding encryption, follows the same mode structures, emphasizing the importance of choosing the right mode based on network environment and security needs.
Real world examples
Example 1: Silotech group’s transition to SFTP: in 2024, Silotech Group, an IT consulting firm based in San Antonio, Texas, switched from FTP to SFTP due to firewall issues and the need for enhanced security. This transition simplified their firewall management and improved their data security, ensuring compliance with regulatory standards.
Example 2: HSBC’s compliance upgrade: HSBC, a major financial institution in the UK, adopted SFTP in early 2024 to comply with GDPR and other data protection regulations. This move ensured the encryption of sensitive financial data during transfer, reducing the risk of data breaches and ensuring regulatory compliance.